Mariam Coladonato
Lead Product Marketing Specialist for Phoenix Contact
In this edition, we talk with Mariam Coladonato, lead product marketing specialist for Phoenix Contact, which manufactures electrical components and products for automation and control. She explains their mGuard technology – which allows remote access to installed components for automation and control. It represents a whole new dimension for plant automation, maintenance, and control: Infrastructure as a Service (IaaS).
Could you provide an overview of mGuard technology, specifically the hardware, the mGuard secure cloud, and the industrial VPN the technology utilizes?
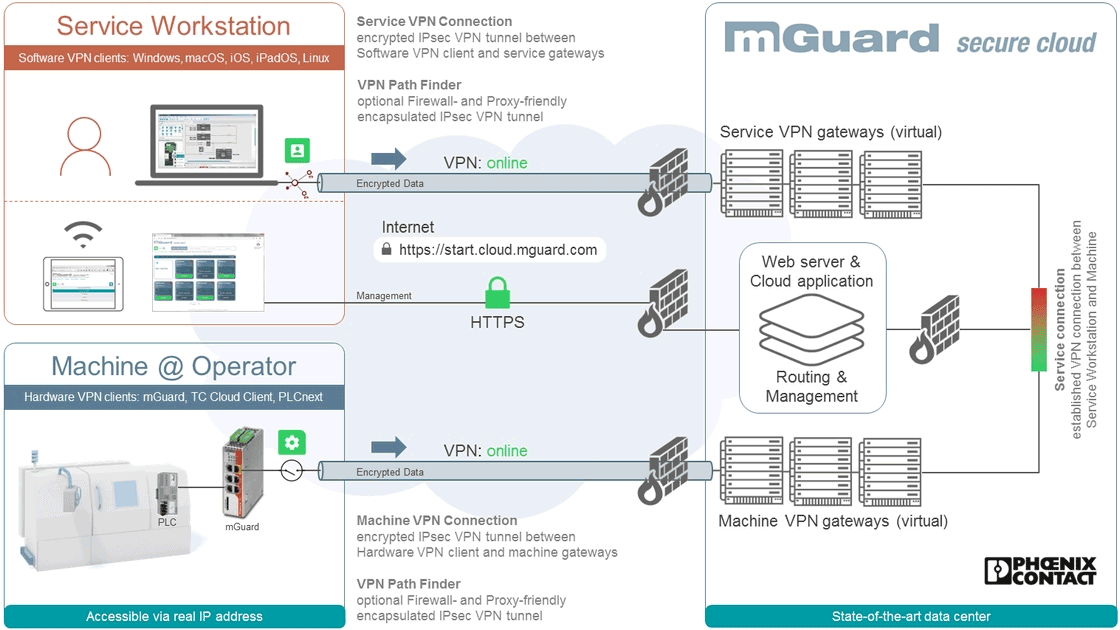
The FL mGuard from Phoenix Contact helps reduce cybersecurity risks in industrial networks. The mGuard includes an uncomplicated, powerful, flexible, and fast firewall. In addition, the VPN functions (IPsec and OpenVPN Client) enable secure remote connections over the Internet for troubleshooting, maintenance, and support.
Phoenix Contact offers several mGuard options to meet different application requirements. The mGuard utilizes several form factors for industrial and commercial applications, including DIN rail-mount, PCI cards, gigabit, fiber, 19-inch rack, and USB-powered. There are additional licensing options for up to 250 VPN tunnels, Deep Packet Inspection firewall, CIFS Integrity Monitoring for OS, and more. Other options include central management software, secure VPN client, and cloud solutions.
The mGuard Secure Cloud™ (mSC) is an industrial VPN Cloud service that works as an Infrastructure as a Service (IaaS) model. It is an easy, cost-effective, and reliable solution for OEMs and machine builders, allowing them to talk securely over the Internet to equipment such as PLCs, HMIs, etc., all over the world. With the mSC, our customers no longer need to send technicians to remote locations for on-site support, significantly reducing travel time and expenses.
Our mSC uses a VPN tunnel from your machines using the supported hardware (FL mGuard or TC Cloud Clients) and another tunnel from your technician’s computer or smartphone to create a secure link, allowing fast and reliable communication. Using mSC is easy because Phoenix Contact acts as your IT department. We build the hardware and software configurations for you based on a few pieces of information you provide, such as the IP network your machine uses. Our mSC service is free, but to take advantage of the service, users need to register an account and purchase the supported hardware and software.
What are some salient benefits of enabling remote access into a machine or equipment remotely?
Remote access has many benefits and advantages. First and foremost, remote equipment is now available from any location. Because technicians no longer must travel to service machines, the user can reduce travel costs by redirecting technician and engineering resources to save time and increase productivity.
The OEM accesses and controls the remote machines in just a few clicks. The equipment typically does not need to be adapted to meet the network settings, only the VPN gateway, so it is easy to integrate into customer networks. Faster service means less downtime for the end-user, which can ultimately result in greater customer loyalty.
The mGuard’s firewall function protects the operator network from unauthorized access. The mGuard includes a VPN NAT feature to quickly resolve IP address conflicts.
When the data (or device) access is by someone other than the asset owner, does this complicate such a configuration? Or is it more welcome because of the subsequent benefit such access provides?
Additional steps must be taken to add users into the remote connection; however, with services like the mGuard Secure Cloud, where most of the configuration and actions are provided, it doesn’t have to be complicated. In this case, the mSC account owners must add these users. Once added, users log in and connect to the existing account, as the remote gateways are already setup.
When the OEM gives the machine owner access to the equipment, it is because they request it. At the end of the day, that piece of equipment is theirs to access. The mSC offers the OEMs a built-in feature called User Restrictions, where this request is fulfilled securely – the end-user cannot see other equipment within the same account.
There’s much concern nowadays about cybersecurity. Industrial networks pose a heightened concern for critical infrastructure and are often found in parts of an organization’s network where cybersecurity resources are not always adequately allocated. What is your perspective on such concern? How might such risk be mitigated?
The IIoT movement helps asset owners increase understanding of their processes to improve productivity and reduce downtime. However, IIoT means that those systems must be connected. The downside is that interconnecting those ICS systems to an enterprise network or even out to the Internet increases cyber risks. This makes industrial processes vulnerable to any internal misconfiguration and even external threats.
However, I believe that asset owners can take advantage of all the IIoT benefits while still applying cybersecurity controls. These security controls vary in an industrial network; they also depend on the type of industry and process. It is essential to follow a defense-in-depth concept that encompasses items like the implementation of industrial firewalls for network segmentation, secure physical port, and cabinet access; use central management software for visualization and monitoring of events, logs, and network security status.
In a pandemic environment, has there been a newfound interest in mCloud technology as it affords remote monitoring and other features such as troubleshooting, without necessarily requiring human contact with the system or cell?
The remote connectivity idea in ICS systems always existed, from old modems to today’s use of cellular and the Internet. The pandemic environment created a greater need to use it.
Due to stay-at-home orders, users and their end customers limited contact. What before might have been a “10-minute drive down the street” for support now must be done remotely. The need increased for secure remote connectivity and cloud-based applications in the current times.
With the advent of 5G and other new protocols, what will be the impact on industrial operations such as manufacturers and other operators?
5G is one of the essential technologies helping industrial companies digitally transform via IIoT. 5G will enable millions of devices to communicate on the same network (massive machine-type communication), blazing fast speed up to 10 Gbps (enhanced mobile broadband) and < 1-millisecond latency (ultra-reliable low latency communication). These three pillars are the driving forces behind the innovation enabled by 5G.
- MMTC enables every machine in the factory to be outfitted with several IoT sensors that can communicate and share data with other devices on the network or do local edge computing.
- Enhanced mobile broadband will enable high bandwidth applications (e.g., AR/VR).
- URLLC will let critical assets communicate with each other autonomously without worrying about latency (e.g., remote-controlled e-stop).
Industrial companies will need to build and deploy private 5G stand-alone networks to take full advantage of these features. A stand-alone network means the company has complete ownership of the 5G network core and radio access network. This ownership provides increased network security, as only approved devices can communicate on this network. All other communication from the outside is blocked. This dedicated network also means that the wireless spectrum is not shared by anyone else, thus improving availability and reliability. Antennas can also be strategically deployed to avoid any dead spots or areas of poor reception.
However, 5G is a new and upcoming technology and must overcome some hurdles before all of this becomes a reality. The first hurdle is releasing the full 5G standard. The 3rd Generation Partnership Program (3GPP), the governing body that releases cellular standards, as of today, only published release 15 and release 16 of the 5G standard. The third and final release, release 17, is still in the works. Release 16 was published at the end of 2020, and therefore, most of the hardware on the market is only compatible with release 15 features.

New hardware supporting release 16 and 17 will need to be thoroughly tested to identify any functional limitations.
The second major hurdle for deploying 5G will be the upfront capital expenditure to deploy the network. First, dedicated spectrum will need to be purchased from the FCC or leased from a network operator. Infrastructure for the 5G network core and radio access network will need to be bought and deployed. Finally, 5G-enabled routers and sensors will need to be deployed inside various networked assets.
In summary, 5G promises increased scalability, reliability, availability, security, and speed; however, much of this technology still needs to be developed and will come with a significant deployment cost once available.
Is there much potential for industrial operations and environments for mCloud technology, particularly its wireless capabilities? How so as we unfold into a new year after a very tumultuous one?
Remote connectivity and data analysis are the most prominent trends that encompass industrial automation in cloud applications, specifically using data management for predictive maintenance and improved performance in the processes. However, these solutions are IT-oriented and met by connecting your industrial devices through routers, cellular modems, and wireless technology all the way out to the Internet, which circles back to the cybersecurity need. Even though the potential for cloud technology seems to be increasing, we must weigh the risks, such as loss of production and machine safety, before any implementation.
The year 2020 pushed everyone to “work remotely,” even industrial applications. Secure remote connectivity through an industrial VPN gateway like the mGuard, together with the mGuard Secure Cloud service, provides secure remote connectivity to your equipment with minimal interaction from users where it is installed.
Additional Links: